
| Basesoft |
| Products | Services | Company | Research | Jobs |
Basesoft SSL HowTo (under construction)
This Basesoft SSL HowTo page gives some more detailed instructions about how using secured access to specific area served by the Basesoft web solutions. This includes both usage of server certificates as well as user certificates for authentication (e.g PKI deployment).
Installing the trusted Root CA certificate
Firefox > 38.1.0 and SSL renegotiation problem
Firefox > 4 and SSL renegotiation problem
Installing and using your personal client certifcate
Security Issues - Certificates, Protecting Private keys
Why does my 2048-bit private key not work
Notes on Encryption Ciphers (256 vs 128 bit, AES etc)
Notes on Certificates formats and Mobile Devices
Incompatibility Issues with Nexus Personal 4.0.1, 4.2.3
Windows Phone 8.1 Error Code 80072F30 when syncing mailbox
../ Back to SSL Secure Pages Overview
In Internet Explorer, with your browser, point to the address of the certificate and save the file on your disk. Double click on the file and the Certificate Installation wizard will start. Because the certificate is self-signed, Internet explorer will automatically install it in the Trusted root Certificate Authority list (it it does not, select the "Trusted Root Certification Authorities" found in Internet Options -> Content -> Certificates). From now on, Internet Explorer won't complain and any Certificate signed with this root CA Certificate will be trusted too. You can also open it from Internet explorer, which will display the certificate. Click on the button Install Certificate to launch the Certificate Installation wizard.
A note on trust (also see Security Issues below). A certificate is digitally signed by an issuer (this might be a CA). There could be a chain of certificates / signers until the Root of the tree is reached (i.e. Top of the chain is found). This Root certificate is always self-signed. Your software (e.g. Windows, Internet Explorer, Firefox) will consider a Root (CA) certificate "safe" if it is stored in its "Trusted Certificate Store". To make PKI and asymmetric encription secure the public key (and certificate) must be exchanged in a separate authentic channel. This means that you should only install Root CA certificates for the issuers that you trust, and verify that those CA certificates (and Public Kyes) are authentic with the issuer by some other means (some other channel) than where you got them. Be aware of certificates that are installed automatically by your software. There is no guarantee that they really are authentic e.g. Versign or Microsoft although they might say so. [Updated 2011-JUN-12]
Firefox > 38.1.0 and SSL renegotiation problem
The temporary fix for Firefox 4 and later as descibed below does no longer work with Firefox 38.1.0 and later. The support for the option (user_pref) "security.ssl.renego_unrestricted_hosts" has been removed from the Firefox source code. Firefox will only allow the same web server to serve http: or https: URLs but not switchning between https: plain password authentication and https: authentication with user (client) certificate. The Basesoft Secure (Authorized Access) Areas require user certificate authentication.
If you experince this problem, e.g. get an error message like this:
An error occurred during a connection to www.basesoft.se.
Renegotiation is not allowed on this SSL socket.
Error code: SSL_ERROR_RENEGOTIATION_NOT_ALLOWED
Then you may use another port, i.e. https://www.basesoft.se:444/sectest instead of just https://www.basesoft.se/sectest. When you already have establised access to a Secure Area, that you have authorization to access, you will also have access to the Public areas. So this is only a one per session action to be performed.
[Updated 2015-JUL-14]
Firefox > 4 and SSL renegotiation problem
You may experience a problem after upgrading to Firefox 4 (and later versions at least up to version 9.0.1) when trying to access some SSL (https://) protected server areas. This is due to the fact that you might have accessed a page as http://something but the area is protected and requires https://something. To make this conveniant for you the web server tries to rewrite such requests to what it should be. This will introduce a re-negotation of the communication between your Browser and the Web server.
As you might be aware of, a flaw in the SSL/TLS protocol was detected in 2009. Firefox 4 tries to protect you from this possible flaw [read more about this].
To temporarily fix your problem, e.g. add the following to your prefs.js file:
user_pref("security.ssl.renego_unrestricted_hosts", "www.basesoft.se,base.basesoft.se,www.fmgtp.se");
In e.g. Windows 7 and when using Firefox 4 (or later) you will find the file prefs.js in:
%USERPROFILE%\Appdata\Roaming\Mozilla\Firefox\Profiles\nnnnnnnn.default\
where nnnnnnnn is some random octal number. [Updated 2011-JUN-13]
You might experience the same problem logging in to the Nordea internet banking. A temporary fix would be to also add "pki-eplusgiro.plusgirot.se", as above, to your prefs.js:
user_pref("security.ssl.renego_unrestricted_hosts", "www.basesoft.se,base.basesoft.se,www.fmgtp.se,pki-eplusgiro.plusgirot.se");
[Updated 2012-FEB-06]
Installing and using your personal client certificate
You may use an authorized certificate issued by some approved organization (and trusted) by Basesoft. Or you may use a personal certificate issued by Basesoft.
Your certificate is stored in a so called Security Device or Token. This could be a hardware token (a smart-card), accessed by a smart-card reader, or a file stored on a disk and managed by a software security device (i.e. SmartTrust Personal, if you have a Swedish Internet Bankning account). Some Web Browsers (i.e. Firefox, Netscape 7.2) also have a (software) built-in Security Device which can hold your certificates and private keys for you.
If you have a smart-card, the certificate(s) and private key(s) are stored on the smart-card. The smart-card (i.e. access and use of the private key(s)) is protected by a PIN.
If your certificate and private key(s) are "soft", they are often distributed in a ".p12" file. This file is protected by a import/export passphrase (or a password). This file may be used in two ways, as a "simulated" hardware device (i.e. with SmartTrust Personal) or imported into i.e. Firefox store.
If you import it into the Firefox Software Security Device, you should choose Software Security Device as the token. Below you will see what simulated hardware tokens look like (i.e. named "Basesoft Jaan", "SHB Jaan", which you name by your self), and one example of a hardware token (SmartTrust Smart Card). The Netscape built-in Security Device that holds all your passwords, private kyes etc should be protected by a good passphrase.
Please be aware of the security risks in using "soft" devices. See Security Issues below.
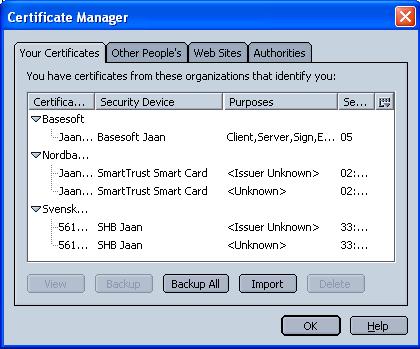
You could also manage your ".p12" file as a simulated hardware token. I.e. you may use SmartTrust Personal -> Administration Utility to "link to" your certificate and private key in the ".p12" file. The SmartTrust certificate mover, "moves" your certificate for use into your Web Browser (i.e. Firefox or Internet Explorer). Note that after "importing" your certificate this way, you need to re-boot your system (i.e. PC).
Using Secure Imap Mail
You may access your Basesoft mail account by a Secure IMAP protocol, e.g. a challenge-response authentication protected by SSL server authentication and encryption. Note that plain text password authentication is no longer supported.
For Pine (e.g 4.61) your host (computer) must be configured with the Basesoft mail server certificate. This is supposed to have been done by your system administrator.
You configure pine by changing your inbox-path, i.e. setting:
inbox-path={MAIL.basesoft.se/ssl/user=USER}inbox
where MAIL is the mail server host name (i.e. base, lacie),
and USER is your mail account name.
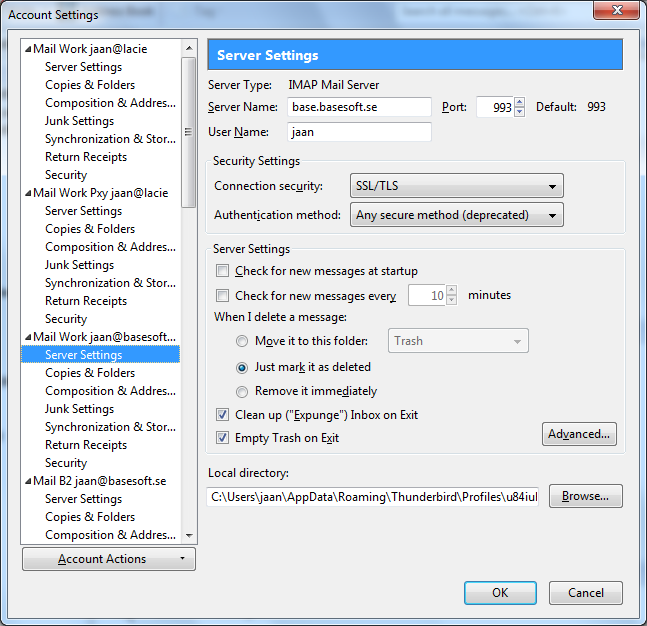
In Thunderbrid (or Netscape (e.g. 7.2) you must set or update your settings in:
Your Account -> Mail & Newsgroups Account Settings: Server Settings : "Use secure connection (SSL)" and "Use secure authentication". This might look something like the image below.
Security Issues - Certificates, Protecting Private keys
Check that the Basesoft server (i.e. *.basesoft.se) certificate is authentic depending on the services/server you are connecting to. The server certificate must have been signed by the Basesoft Certificate Authority (CA). You must hence first have installed the Basesoft CA certificate on your computer (e.g. in Netscape). Please verify the the SHA1 Fingerprint of "Basesoft Root CA04" (the CN, Common Name) is DE:57:A6:4E:82:A9:4D:5D:28:F6:29:17:BF:6A:0A:35:77:ED:E4:14 or the SHA256 one is D3:34:C8:14:56:CF:07:C2:86:6C:9D:22:0E:56:2D:0F:3D:80:EF:C6:59:4A:10:24:E3:19:70:4D:57:B0:D7:66.
In some cases you need to authenticate yourself by a personal ("client") certificate and private key which need to be available on some kind of a security device/token (i.e smart-card, p12-file).
Please be careful with "soft" software security tokens, i.e. ".p12" files. If you have such a passphrase-protected file, someone can "borrow" it, and crack the passphrase silently somewhere else. Next the "hacker" may inpersonate as you. You might also have some "logger" software on your computer that "snoops" your passphrase making it easier to "borrow" your certificate and private key.
Do not access secure pages from an unsecure computer, i.e. an internet cafe. Your Browser, or Mail reader, will certainly cache files on the un-trusted computer in un-encrypted plain text form.
As of 2012-APR-30 This site uses a new CA-certificate, "Basesoft Root CA04". The server certifcates are new and signed by this new CA. If you have a personal (client) certificate you have to get a new one. [Updated 2012-APR-30]
Why does my 2048-bit private key not work
At the moment Certificates issued by Basesoft as default have 2048-bit RSA private/public keys. This works with at least Netscape 7.2 or later. The private key sizes for SSL may need to be reduced to either 512 or 1024 for compatibility with certain web browsers. If you notice problems, try upgrading your Browser version, and also report the problem to webmaster. Some commercial Smart Card also have restrictions on key length, i.e. maximum 512 or 1024 bits. There might also be problems with some versions of Netscape Navigator and Microsoft Internet Explorer, and with other browsers that use RSA's BSAFE cryptography.
Notes on encryption ciphers
This Basesoft WEB server supports high-grade encryption (i.e. DHE-RSA-AES256-SHA). To utilize this, your Web Browser needs to supports this. I.e. Firefox, Netscape 7.2 and later does so. Microsoft Internet Explorer (i.e. olde versions such as 6.0 XP SP2) only seems to support up to RC4-MD5 (128/128 bits). Both work with TLSv1 (preferred by the Basesoft server) as well as SSLv3 and SSLv2. Note that TLS is Off by default in older versions of MS IE.
Microsoft Windows (XP, W2003SRV does not currently support any encryption ciphers with longer keys than 168-bit (e.g 3DES) nor the more modern AES encryption. So you may considering upgrading Windows and Internet Explorer.
AES seems to be the current de-facto standard of encryption. NIST (National Institute of Science and Technology) states, “Assuming that one could build a machine that could recover a DES key in a second (i.e., try 255 keys per second), then it would take that machine approximately 149 thousand-billion (149 trillion) years to crack a 128-bit AES key. To put that into perspective, the universe is believed to be less than 20 billion years old.” AES was selected out of five finalists algorithms, each of which were technically secure. Originally titled Rijndael, AES had its start as an algorithm named Square, which was enhanced by Joan Deamen and Vincent Rijmen. It was selected because it was fast, simple, secure, and versatile. It is a block cipher that uses 128, 192, and 256-bit symmetric keys to encrypt data.
RC4 is a symmetric key streaming cipher created by RSA. This cipher is often used in the SSL (Secure Socket Layer) encryption used on the internet by some websites. It is also included with the Microsoft base Crypto API. RC4 can use a 40-bit to 128-bit keys, which means its strength can vary as well. While 40-bit encryption is available, it is not recommended for sensitive data because RC4 40-bit encryption can be brute force cracked in a relative short period of time (i.e. 1 day to 2 weeks).
Notes on Certificate formats and Mobile Devices
This Basesoft WEB server uses Certificates, CRLs etc encoded in PEM (a kind of ASCII) format. Some mobile devices (e.g. Sony Ericsson Mobile Phone) seems to have problems with this format. They need this data encoded in DER (a kind of BINARY) format instead. This means that you may not be able to view this page from your mobile phone. To make this work you have to download the Basesoft Root CA certificate and the WWW server certificate in DER format to your phone. If you have this problem, please mail Basesoft, and we will send you this information in DER format.
Incompatibility Issues with Nexus Personal 4.0.1, 4.2.3
The Swedish bank Handelsbanken has upgraded its "security program" to Nexus Personal 4.0.1/4.2.3 (including a kind of soft certificate PKCS#11 token container, similar to that of e.g Netscape 7.2 Software Security Device). You have to install it when you are asked to renew your old "soft" (file) Handelsbanken authentication (client) certificate.
Now you also at the same time might be running the previous SmartTrust 3.4.10 software, which you do if you use "hard" smart card authentication, e.g. electronic ID from the Nordea bank. After installing Personal you no longer will be able to use your smart card ID. The workaround for this is killing the Personal 4.0.1/4.2.3 daemon process that keeps appearing in your Windows Notification Area. You simply right-click on it at select Exit. Or you may stop it by the Task Manager, where the Process "name" is "Personal.exe". After stopping it everything works again. You do not need to restart Personal. It starts when you want to use the Handelsbanken certificate the next time, or by itself after a while (you might wonder why).
Instead of running Personal at Windows login (startup) you should continue to run SmartTrust 3.4.10 Certificate Mover to have all your applications, e.g Nordea Axess, to find your smart card. You may consider removing the login startup of Personal from e.g. DriveLetter:\Documents and Settings\All Users\Start Menu\Programs\Startup, then you need not stop in manually.
You also may notice that you did not get the opportunity to decide where to install the Personal software executables. For those of you that do not want to fill your Windows Drive with all kinds of software, it did land in e.g. DriveLetter:\Program Files\Personal\bin\. The startup link, Personal, points to Personal.exe in that directory, which also is the "Start in:" folder for the link ("shortcut") - this if you would like to re-create it some day.
The installation of Nexus Personal also changes the default startup program and file icon for .p12 files to itself without asking for confirmation, which is not nice behaviour, either. You may not want all your .p12 files to be opened by Nexus Personal, since the use of Personal probably might be more limited than the configuration you hade before installation of Personal.
As before, you will not be able to log in to Handelsbanken if your e.g. Nordea smart card ID is inserted into the smart card reader, just take it out, and it works. So in some way the problem now is symmetric. [Updated 2006-FEB-16]
Windows Phone 8.1 Error Code 80072F30 when syncing mailbox
If your mail server (e.g. IMAP4 with SSL, i.e. imaps) has got a new server certificate, e.g. when the old one has expired, the mailbox syncing on your Windows Phone 8.1 will stop working. You will get error code 80072F30, and a text message hinting on a certificate problem.
To workaround this bug you have to delete the old account and recreate it again. Note that you can not create a new account with an other name (e.g. "MAIL 2") with the same mail account name (e.g. nnn@site.foo) unless the old account is deleted first. Select "advanced" to set up the account again. Note that the setting up process will take 10-15 minutes. During this time the phone will try to log in many times to the mail server and fail. Finally (after 10 minutes or so) it will detect that it needs to accept a certificate, which you may OK.
Usefull settings are to set the Incoming mail server to e.g. mail.site.se:993 (imaps), and check Server Requires Authentication and to Use SSL. You may also have to specify the port for the outgoing mail (smtp) server, e.g. mail.tele2.se:587.
[Updated 2015-MAY-13]
../ Back to SSL Secure Pages Overview
| |
Copyright © 1998-2025 Basesoft Open Systems AB, SWEDEN |
|
||